Learn more about the course
Get details on syllabus, projects, tools, and more

Professional Certificate in Cybersecurity
Learn from World-Renowned JHU Faculty
Application closes 10th Jun 2025

PROGRAM OUTCOMES
Level up your career with actionable cybersecurity skills
-
Understand foundational and core cybersecurity principles
-
Learn to implement security controls for protecting enterprise networks
-
Evaluate cloud security and develop comprehensive strategies for cloud data security
-
Master key ethical hacking methodologies
-
Learn how AI-driven tools are used in cybersecurity through practical use cases
-
Learn secure software development techniques
-
Implement appropriate security controls for safeguarding applications
Earn a certificate from Johns Hopkins University
KEY PROGRAM HIGHLIGHTS
Why choose the Professional Certificate in Cybersecurity program
-

Earn a certificate from a top-ranked university
Earn a certificate from the prestigious Johns Hopkins University, learning from world-class faculty and industry leaders.
-

Industry-focussed curriculum
Master network and infrastructure security, cloud security posture improvement, learn about AI solutions for cybersecurity and more.
-

Flexible learning format
Learn through recorded lectures, monthly live masterclasses by JHU faculty, interactive mentored sessions, and AI-powered learning tools.
-

Hands-on learning through case studies, projects and lab activities
Work on real-world case studies, projects, and hands-on lab activities to build practical cybersecurity skills that employers look for.
-

Get expert mentorship
Gain insights from industry practitioners in cybersecurity, refine your projects and set yourself up for success in the field.
-

Personalized program support
Receive 1:1 guidance from a dedicated Program Manager and academic support from cybersecurity experts.
Skills you will learn
Risk Assessment and Management
Network Security
Cloud Security
Penetration Testing
Malware Analysis
Secure Software Development
Identity and Access Management (IAM)
Incident Response and Forensics
Risk Assessment and Management
Network Security
Cloud Security
Penetration Testing
Malware Analysis
Secure Software Development
Identity and Access Management (IAM)
Incident Response and Forensics
view more
- Overview
- Curriculum
- Certificate
- Tools
- Faculty
- Mentors
- Fees

This program is ideal for
Professionals looking to advance their careers with cybersecurity skills
-
Mid to senior-level IT professionals & engineers
Ideal for those seeking to upskill or cross-skill in cybersecurity. It prepares professionals for roles such as cybersecurity architects, senior engineers, or those on a CTO track.
-
Early to mid-career cybersecurity professionals
Designed for early to mid-career cybersecurity professionals who want to upskill, stay ahead of evolving threats, and transition into mid-senior cybersecurity roles.
-
Technology leaders & decision-makers
Ideal for IT leaders seeking advanced skills to strengthen their organization’s cybersecurity strategy against modern threats.
-
Architects & technology consultants
Suited for professionals with strong technical backgrounds seeking comprehensive cybersecurity expertise in their domain.
Experience a unique learning journey
Our pedagogy is designed to ensure career growth and transformation
-
Learn with self-paced videos
Learn critical concepts from video lectures by faculty & cybersecurity experts
-
Engage with your mentors
Clarify your doubts and gain practical skills during the weekend mentorship sessions
-
Work on hands-on projects
Work on projects to apply the concepts & tools learnt in the module
-
Get personalized assistance
Our dedicated program managers will support you whenever you need
Syllabus designed for professionals
Designed by the faculty at Johns Hopkins University
Preparatory Module
This module will set learners up with all the tools needed for their learning journey and build a solid foundation in 3 essential domains: Operating systems, applications and APIs, and cloud computing.
Module 1: Foundations of Information Security
The outcome from this module is to learn the fundamentals of cybersecurity by studying the most relevant models and frameworks used worldwide. Gain insights into the intricacies of the underlying technologies such as Cryptography, Authentication & Risk Management. Comprehend the evolving threat landscape by exploring different attack vectors such as password brute-force, data manipulation, and Ransomware attacks.
Week 01: Core Cybersecurity Principles & Frameworks
Get introduced to foundational concepts of cybersecurity by understanding the core principles and security frameworks. Learn fundamentals of Cryptographic methods and authentication mechanisms.
Topics Covered:
- CIA Triad
- Risk Management
- NIST Cybersecurity Framework 2.0
- IAAA
- Emerging Trends in Cybersecurity
- Careers in cybersecurity
Sample Case Study: The Equifax Data Breach (2017)
Sample Project: Mapping events from Equifax Data Breach with NIST 2.0
Week 02: Cryptography & its Applications
This week, participants will learn cryptographic techniques, encryption/decryption, and hashing. They will examine the evolution of cryptographic algorithms. Also, participants will be introduced to digital signatures and certificates.
Topics Covered:
History and Evolution of Cryptography
Encryption & Decryption
Types of Cryptographic Algorithms
Hashing
Digital Signatures & Certificates
Sample Case Study: HSM in the payments industry
Sample Project: Create keys and certificates using OpenSSL
Sample Lab Activity: Cryptography using CyberChef
Week 03: Threat Landscape & Adversaries
This week, various cyberattacks and threat actors will be introduced to the participants. By the end of the week, participants will be able to identify various types of malware, ransomware, cybercrime actors, and learn about physical attacks.
Topics Covered:
- Types of cyberattacks
- Organized Cyber Crime
- Ransomware - A global threat
- Nation-State sponsored adversaries
- Physical Attacks
Sample Case Study: Colonial Pipeline Attack (2021)
Sample Project: Ransomware threat research
Week 04: Cyber Attack Techniques
This week delves deeper into specific attack vectors on various IT functions of an enterprise. Participants will explore attack methodologies using the MITRE ATT&CK framework, social engineering, cryptographic, and endpoint attacks. Participants will also be able to comprehend cyber attackers' usage of Gen-AI.
Topics Covered:
MITRE ATT&CK framework
Social Engineering Attacks
Cryptographic Attacks
Attacks on Endpoint
Attacks on Data
AI-powered Threats
Sample Case Study: Salt Typhoon attack on the US Telecom sector 2024
Module 2: Network & Infrastructure Security
The outcome of this module is to learn how the networks that connect organizations and continents together work. You would be exploring the different ways of designing the networks by following best practices in security. Network resilience and redundancy are an emerging trend, and this is something that is covered in this module as well.
Week 05: Security Architecture
This week starts with the journey into the basics of computer networks and explores network security fundamentals and resilience strategies. By the end of this week, participants will be able to comprehend zero-trust network architecture and be able to implement secure network policies.
Topics Covered:
- Foundations of Computer Networks
- Network Redundancy and Resilience
- Secure Network Design
- Zero Trust Network Architecture
- Network Segmentation & Demilitarized Zones
- Network Security Policies and Compliance
- Network-based Attacks
Sample Case Study: The Largest DDoS Attack
Sample Project: Analyzing network diagrams
Week 06: Perimeter Security
This week delves into the nuances of perimeter security, covering Firewalls, Intrusion Detection & Prevention Systems, and Virtual Private Networks. This week will allow the participants to explore advanced security configurations and network hardening techniques.
Topics Covered:
Next Generation Firewalls
IDS and IPS
Virtual Private Network
Sample Lab Activity: Configuring a firewall with iptables
Week 07: Security Monitoring
This week focuses on infrastructure and network security monitoring techniques, where the participants will learn about continuous security monitoring with advanced threat detection. Participants will be able to delve deeper into monitoring systems such as SIEM and will be able to monitor the signs of ongoing cyber attacks within a network.
Topics Covered:
Network Traffic Monitoring
Network Configuration and Change Monitoring
Vulnerability Management
SIEM & EDR
Sample Case Study: Log4j zero-day vulnerability
Week 08: Identity and Access Management
This week will allow the participants to understand authentication mechanisms, identity lifecycle, and access control models. Upon completion of the week, participants will be able to plan authentication methodologies for various systems.
Topics Covered:
Authentication Systems and Protocols
Active Directory
Identity Lifecycle Management
Sample Case Study: 23andMe Credential Stuffing
Week 09: Specialized Security Protocols
The final week of the module covers important security protocols such as WLAN, SSH, and IPSec. This week will expose the learners to such security protocols, which will enable them to cater to advanced network configuration and hardening techniques.
Topics Covered:
WLAN Security
IPSec & SSH
DNS Security
Sample Case Study: GitHub SSH Key Leak Incident (2023)
Sample Project: Compare and contrast network security protocols
Module 3: Cloud and Data Security
The outcome from this module is to learn how to build & manage the cloud infrastructure for an enterprise. You would be learning about the security challenges with cloud implementations. You would also be learning about the basics of Cloud security mechanisms to improve cloud security posture.
Week 10: Cloud Fundamentals
This week, the participants will be exposed to the foundational concepts of cloud computing. This week will allow learners to learn about cloud deployment strategies and comprehend security risks associated with cloud computing.
Topics Covered:
Cloud Computing Definitions
Cloud Deployment Models
Cloud Migration Strategies
Threats to Cloud Security
Basics of Cloud Security Mechanisms
Week 11: Secure Cloud Design
This week, the participants will discover secure cloud architecture principles and cloud-native security services. This week will allow learners to be able to apply methodologies to ensure a secure cloud architecture is implemented, along with strong identity and access management systems.
Topics Covered:
Secure Cloud Architecture
Cloud Native Security Services
Cloud Security Alliance
IDAM in the cloud
Sample Case Study: Capital One data breach (2019)
Week 12: Cloud Posture and Security
This week will focus on cloud security posture management and resilience strategies. Participants will explore government cloud security frameworks.
Topics Covered:
Cloud Security Posture Monitoring
Resilience in Cloud
AWS GovCloud (US) and Azure Government Cloud
Sample Case Study: Microsoft Exchange Online Breach (2023)
Sample Lab Activity: Monitor virtual machine activity with AWS CloudTrail
Week 13: Cloud Data Security
The final week of the module will delve into data security concepts, covering data classification, encryption, and data protection in the cloud. Upon completion of this week, the participants will be able to develop the ability to select appropriate protection mechanisms for cloud data security.
Topics Covered:
Data classification and securing specific storage types
Data protection mechanisms on Cloud (Encryption, Masking, and Anonymization)
Secret Management
Confidential Computing (Protection for data in use)
Sample Case Study: Cognizant S3 Bucket Exposure (2023)
Sample Project: Using S3 buckets for secure storage of sensitive data
Module 4: Ethical Hacking & Penetration Testing
In this module, you'll learn to conduct structured security assessments and craft high-quality penetration testing reports, ensuring clarity, accuracy, and actionable insights. This module equips you to identify, assess, and exploit vulnerabilities in systems, networks, and applications while adhering to ethical hacking standards. You’ll gain hands-on experience with penetration testing, including reconnaissance, scanning, and enumeration to identify attack vectors.
Week 14: Planning & Authorization
This week, the learners will be able to understand the penetration testing lifecycle, scope management, and reporting. Upon completion of this week, the participants will be able to comprehend the ethical hacking methodologies and understand the various processes involved.
Topics Covered:
Need and Life Cycle of Penetration Testing
Ethical Hacking Methodology
NIST SP 800-115 and Penetration Testing
Scope Management & Authorization Management
Report generation and mapping
Sample Project: MITRE ATT&CK Matrix for Enterprise & DoD ZT capabilities
Week 15: Reconnaissance & Mapping
This week will help the participants learn about network scanning, host discovery, and vulnerability scanning techniques. These techniques will help to build strong core concepts of the initial steps of an ethical hacking lifecycle.
Topics Covered:
Network Scanning and Host Discovery
Vulnerability Scanning and Reporting
Application Mapping
Sample Lab Activity: The Packet Sniffing and Spoofing Attack Lab
Week 16: Penetration Techniques
This week covers hands-on aspects of types of penetration techniques. Participants will learn about infrastructure penetration testing and web application penetration testing. This week also delves into wireless penetration testing practices.
Topics Covered:
Infrastructure Penetration Techniques
Web Application Penetration Testing
Wi-Fi Penetration Testing
Sample Lab Activity: SQL Injection (SQL) lab
Week 17: Exploitation & Persistence
The final week of this module will cover the final aspects of the ethical hacking lifecycle, which are exploiting vulnerabilities, maintaining persistence, and exfiltrating data. The participants will learn about lateral movement techniques and methods to cover tracks during penetration testing activities.
Topics Covered:
Exploiting Vulnerabilities
Post exploitation
Persistent access
Exfiltration & Impact
Covering your tracks
Sample Lab Activity: Exploiting Eternal Blue Vulnerability
Module 5: AI for Cybersecurity
With this module, you would gain a foundational understanding of AI and machine learning, exploring their applications in cybersecurity to enhance threat detection, risk assessment, and automated defense mechanisms. You would also learn about key AI frameworks and tools used in security operations, enabling efficient monitoring and response strategies. Additionally, analyze the principles of responsible AI adoption, addressing ethical considerations, privacy concerns, and potential risks associated with integrating AI into enterprise environments.
Week 18: Introduction to Machine Learning and Artificial Intelligence
This week introduces the participants to the basic constructs of Machine learning and the foundational concepts of Artificial Intelligence. The participants will understand the application of these concepts in cybersecurity. Participants will also explore AI-based fraud detection and phishing prevention.
Topics Covered:
Machine Learning Models and Artificial Intelligence
Utilizing AI for Security
Generative Adversarial Networks (GANs)
Enhancing Vulnerability Management with AI
Using AI for fraud prevention
Detection of phishing emails with AI
Sample Case Study: DeepSeek AI Platform Attack
Week 19: AI Frameworks and Tools
This week will focus on the AI frameworks relevant to the context of cybersecurity. Upon completion of this week, the participants will be able to identify AI-based risks in an enterprise and effectively apply necessary frameworks for risk treatment.
Topics Covered:
MITRE ATLAS
Global Regulatory Landscape for AI
AWS AI features
NIST AI Risk Management Framework (AI RMF)
Sample Case Study: Accelerating Incident Response using GenAI
Sample Lab Activity: Exploiting Gandalf
Week 20: Responsible AI Adoption
This week covers ethical, privacy, and security concerns in AI-driven cybersecurity. This will allow the participants to measure the challenges associated with implementing AI-based security solutions and integrating AI with existing security solutions in an organization.
Topics Covered:
Integrating AI with security controls
Monitoring AI implementation
Ethical concerns in using AI for cybersecurity
Privacy concerns in using AI for cybersecurity
Security concerns in LLMs
Sample Case Study: Purchasing a Chevrolet Tahoe for $1
Module 6: Developing Secure Software
The outcome from this module is to learn how to develop software with a security mindset right from the requirement gathering stage. You will be introduced to secure software development and DevSecOps practices, integrating security into the Software Development Lifecycle (SDLC). You would also learn secure coding principles, application security testing, and software maintenance.
Week 21: Software Development and DevOps
This week, participants will be exposed to the concepts of software development and DevOps. By the end of the week, participants will be able to understand the basic source code controls and comprehend the most important security risks to web applications.
Topics Covered:
Agile Software Development
Introduction to DevOps
Source Code Control
OWASP Top 10
Sample Case Study: T-Mobile API Breach
Sample Project: Create a product selection guide for VCS products
Week 22: Security in Software Development
This week will introduce the participants to security-by-design principles and threat modeling. This week will help the participants to be able to understand the needs and security requirements in the software development process.
Topics Covered:
Review Security Requirements
Security by Design
Building Threat Models
Sample Lab Activity: Build a threat model with OWASP Threat Dragon
Week 23: Secure Coding
This week will cover the basic secure coding principles and will help the participants to gain practical knowledge in secure coding practices, namely Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST).
Topics Covered:
Static Application Security Testing (SAST)
Dynamic Application Security Testing (DAST)
Sample Project: Dynamic Application Security Testing with NMap
Week 24: Software Maintenance and Operations
The final week of the module combines concepts related to the operations and maintenance of applications. Participants will learn software patching, vulnerability management, and configuration security.
Topics Covered:
Continuous Monitoring & Logging
Patch & Vulnerability Management
Web Application Firewalls
Configuration Management
Sample Project:
Find software composition vulnerabilities in Java applications with OWASP Dependency Check.
Create a Docker file and scan it with Snyk to find vulnerabilities.
Master in-demand cybersecurity tools
Tools and techniques you will learn
Earn a professional certificate from Johns Hopkins University
Get a certificate of completion from Johns Hopkins University (with Continuing Education Units - CEUs)

* Image for illustration only. Certificate subject to change.
Meet your faculty
Learn from world-renowned JHU Faculty
Interact With Our Mentors
Engage with leading cybersecurity experts who will guide you in applying cybersecurity techniques to drive business resilience and advance your career in cybersecurity.
Program fee
The Professional Certificate in Cybersecurity fee is 3,800 USD
Invest in your career
-

High-quality learning content from JHU faculty.
-

Live mentored learning in micro-classes (up to 30 learners).
-

Build an impressive, industry-ready portfolio with hands-on projects.
-

Get personalized assistance with a dedicated Program Manager.
Payment Partners
Check our different payment options with trusted partners
*Subject to partner approval based on applicable regions & eligibility
Admission process
Admissions close once the required number of participants enroll. Apply early to secure your spot
-

1. APPLY
Fill out an online application form.
-

2. REVIEW
Your application will be reviewed by a panel from Great Learning to determine if it is a fit with the program
-

3. JOIN PROGRAM
After a final review, you will receive an offer for a seat in the upcoming cohort of the program.
Batch Start Date
-
Online · To be announced
Admissions Open
Delivered in Collaboration with:
Johns Hopkins University is collaborating with online education provider Great Learning to offer the Professional Certificate in Cybersecurity. Great Learning is a professional learning company with a global footprint in 170+ countries. Its mission is to make professionals around the globe proficient and future-ready. This program leverages JHU's leadership in innovation, science, engineering, and technical disciplines developed over years of research, teaching, and practice. Great Learning manages the enrollments and provides industry experts, student counselors, course support and guidance to ensure students get hands-on training and live personalized mentorship on the application of concepts taught by the JHU faculty.
Batch Profile
The PGP-Artificial Intelligence and Machine Learning class represents a diverse mix of work experience, industries, and geographies - guaranteeing a truly global and eclectic learning experience.
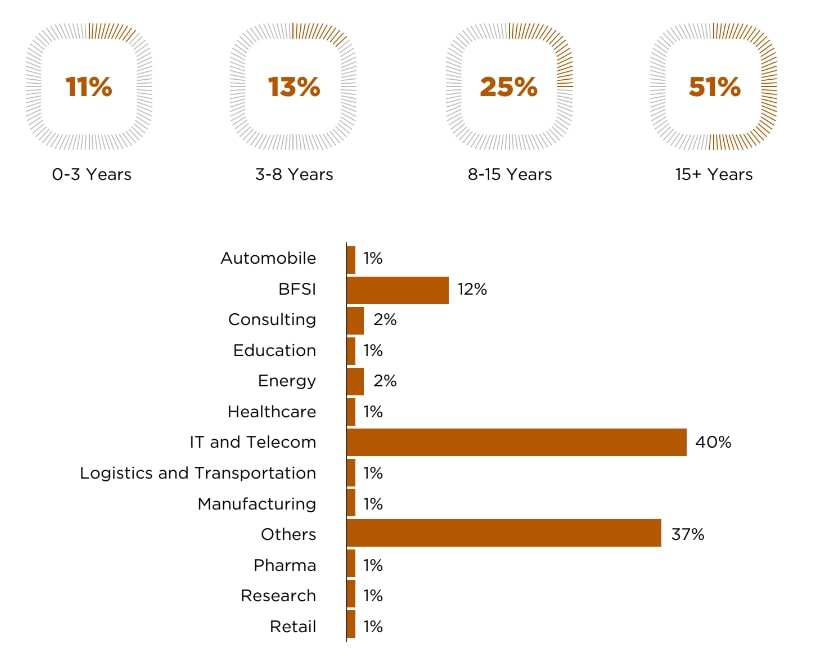
The PGP-Artificial Intelligence and Machine Learning class comes from some of the leading organizations.




 Speak with our expert
Speak with our expert

























